|
|
|
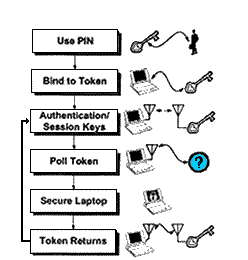
"Mobile devices are susceptible to loss and theft because they are small, light, and easy to carry. Unfortunately, they often contain sensitive data that their owners would prefer to keep private. The consequences of exposing such data range from the inconvenience of canceling credit cards to the public loss of state secrets. If a user were content that data on a missing [mobile device] could not be viewed by unprivileged eyes, he could simply replace the [mobile device] and restore from backup."* Two researchers: Mark D. Corner and Brian D. Noble of the University of Michigan College of Engineering, have conceived of a solution to the security threats posed by the loss or theft of a mobile device called Zero-Interaction Authentication, or ZIA. Currently the solution is designed for use with a laptop but it could be adapted for all mobile devices in the future The focus of their solution is against data security threats posed by the physical possession of a laptop or proximity to it. "Possession enables a wide range of exploits. If the user leaves his login session open, attacks are not even necessary; the attacker has all of the legitimate user's rights." Zero-Interaction Authentication is deigned to eliminate the risks associated with the loss or theft of a mobile device. ZIA utilizes two pieces of hardware: the laptop and an authentication token connected by a short range wireless link to secure the data on the mobile device. As long as the authentication token, which can be worn on a piece of clothing or clipped on to a labcoat pocket, is within range of the computer, the computer's systems function normally. But once the computer is separated from the token, its files automatically become encrypted. "When a user walks away from his laptop to get a cup of coffee, it will sense that he is leaving and begin securing the computer," Noble says. "As he returns, as soon as the user comes within radio range, the [authentication token] will begin unlocking the computer so that it is ready to resume work when the user sits down."
"There are two requirements for system security.
First, a user's token cannot provide key decryption services
to other users' laptops. Second, the token cannot send decrypted
file keys over the wireless link in cleartext form. Therefore,
the token and laptop use an authenticated, encrypted link. ZIA uses common encryption protocols but it is the first know system that liberates the user from the requirements of continuously having to enter and/or update secerity passwords. * Excerpts from the paper "Zero-Interaction Authentication" by Mark D. Corner & Brian D. Noble; Department of Electrical Engineering and Computer Science University of Michigan, Ann Arbor, MI
|
||||||